Anonymous surfing on the Internet
|
Modification
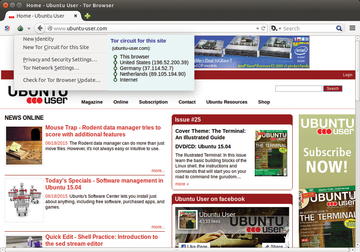
The onion symbol sits on the upper left in the browser next to the address bar. To the left of this symbol is the NoScript icon. As soon as you call up a web page and click on the small triangle next to the Tor icon, you will be able to see which route your data packets take. The route is shown next to the configuration menu and is displayed in the form of IP addresses for the Tor nodes used to transmit data as well as the location of the servers. You will also see that Tor chooses a new route every time another page is called (Figure 3).
Clicking on the icon for the NoScript add-on to the left of the Tor onion, and selecting the Options entry in the menu, opens a rather voluminous dialog containing the tools settings. The developers of the Tor bundle put a lot of careful preparation into NoScript so that the settings are not too restrictive for most websites. However, if a frequently called website doesn't appear correctly because of a lack of rights, then you should enter the URL for the affected site in the options menu under positive list . The add-on for the site will then allow scripts to execute (Figure 4).
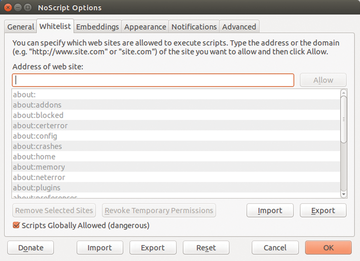 Figure 4: The NoScript add-on makes it possible to deal with the scripts embedded in the websites in a finely grained way.
Figure 4: The NoScript add-on makes it possible to deal with the scripts embedded in the websites in a finely grained way.
You can prevent Microsoft Silverlight, Adobe Flash, Java, and other programs from loading with embedded objects . Remember that overly restrictive settings will cause websites to run incorrectly. Therefore, the browser comes with this filter deactivated. The settings under extended make it possible to fine-tune the behavior of the add-ons. For this, the tool makes a distinction between trustworthy and non-trustworthy sites and defines its own rules by setting or removing checkmarks for the corresponding options.
Additionally, the HTTPS group lets you force or prevent encrypted connections for addresses that you can choose as you wish. But, because the developers of the Tor Bundle have already integrated the Firefox HTTPS Everywhere add-on, the browser already requests the encrypted version of all sites called.
The developers have even modified the customary the configuration dialog for Firefox. As a result, the basic configuration of the browser does not create a browsing history and it does not save passwords. You will find a data transmission function introduced and implemented in more recent versions of the Tor browser in the extension | data transmission tab. However, this is turned off. With this setting, the software does not send status reports to the Tor project. The preset update function in Firefox was modified so that only the search for updates in the extensions | update tab is activated. The updates themselves are not automatically installed.
Advertising and Tracking
Commercial websites can be so cluttered with banners and animated content that the user loses sight of the actual content. Many sites also load so-called web pixels that often, unbeknownst to the user, track user surfing behavior to many other sites.
Firefox offers two effective tools – in the form of the Adblock Plus and Ghostery add-ons – for dealing with these pests [2]. However, the Tor project has not yet integrated them into the bundle. It is a good idea to install these manually. You will find that the browser speeds up because unnecessary DNS queries disappear. It is also smart to add the filter subscription Social Media for Adblock Plus to prevent tracking by social media services like Facebook and Twitter.
« Previous 1 2 3 Next »
Buy this article as PDF
Pages: 3
(incl. VAT)