Kali Linux 2.0
|
Range of Uses
Kali Linux, with its huge wealth of software, covers almost all hardening functions, and they aren't limited to either home network, company intranet, or specific access technology. The system is based on procedures used by professional administrators and makes light work of standard tasks. You will find several useful preconfigured tools such as DMitry, Ike-scan, Netdiscover, Nmap with the graphical front-end Zenmap and p0f that help give you an overview of any network. Maltego, which is used for data mining on the Internet, occupies a special position.
The Vulnerabilities Analysis menu bundles numerous tools that make it possible to locate problematic settings on the network using various test routines. Included is the most comprehensive tool for analyzing vulnerabilities, OpenVAS. The Kali developers have already customized this tool, which is usually complicated and time-consuming to install, to the extent that it is ready for use immediately after completing the initial setup by clicking on the openvas initial setup entry. You will find programs in the Web Applications submenu that you can use to check web applications for vulnerabilities. They include the usual suspects: Burp Suite, Paros, Skipfish, Vega, and w3af, which take care of problems such as SQL injection or cross-site scripting.
Kali Linux primarily lists tools in Database Assessment that you can use to test the security of SQL databases. The programs from the Password Attacks submenu generate attacks of various kinds on passwords and therefore reveal weak and thus insecure authentication credentials. The Wireless Attacks subgroup concerns wireless network security. As well as the legacy kings of the hill, Aircrack-ng and Kismet, the distribution also provides lesser-known programs such as the WiFi crackers Fern and PixieWPS, which try to guess WPS PIN numbers.
You will find other important tools for security audits in the Exploitation Tools and Sniffing and Spoofing submenus. It is possible to vulnerability check computers on a heterogeneous intranet using exploits with the tools offered here. Thanks to programs such as Ettercap and Wireshark you can also sniff network traffic – for example, to determine whether malware has been smuggled in through holes in the firewall. Kali keeps matching applications for remotely controlling Kali in the Establish Access submenu.
You will find appropriate programs in the Forensics group if you suspect that malware has found its way onto the network that you are examining, or if you need to document certain facts for legal evidence. Using these programs, you can both examine target computers for malware, such as rootkits, and also reconstruct data. Firmware files for operating certain hardware and the system's RAM can be examined using these programs, too.
Documented
Above all, forensics experts need to document each step in detail so that others can understand their work. Kali Linux provides a number of useful tools in the Generating Reports group to facilitate these often annoying documentation obligations. The choice is not limited to reporting software in the narrower sense: CutyCapt, for example, records the WebKit rendering of web pages and outputs it different graphics formats.
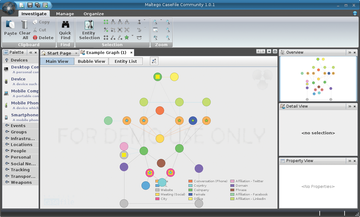
RecordMyDesktop also continuously records the whole screen on request, with audio content if necessary. CaseFile, much like its big brother Maltego, is a data-mining tool that links information from various sources and thus creates a detailed picture of a situation. Finally, you can analyze and document password security using Pipal from the Generating Reports menu (Figure 4).
« Previous 1 2 3 4 Next »
Buy this article as PDF
Pages: 3
(incl. VAT)