Anonymous surfing on the Internet
The Internet is a veritable cornucopia for data collectors of all kinds. Secret service agencies, marketing agencies, and criminals are lying in wait to gather up and abuse the personal data of unsuspecting surfers. In many cases, it is the browser, or the add-ons used by the browser, that provide access by data spies who, through the application of sophisticated website programming techniques, invade and diminish the personal privacy of others.
The standard settings for the typical web browser without protective extensions leave the user wide open to real risks. Surfing habits can be captured and identified. The user is vulnerable to malware attacks. Manually harden the software thus makes sense, but this process requires experience with techniques for guarding against cyberattacks. The Tor browser offers a much simpler solution for users wanting to block snooping and overzealous data collection.
How It Works
The Tor bundle combines several reliable technologies from open source software, thereby achieving a very high level of security. The Tor network and the Firefox web browser function as the central components of the bundle. The Tor team has enriched Firefox with several preconfigured add-ons and then configured the browser so that it searches for access to the Internet exclusively via onion routing. You could manually install both components but that would take a lot of configuration work. Therefore, the Tor browser package is ideally suited for the security-minded user lacking subject matter expertise in cybersecurity and data privacy.
The Tor concept had been developed by the year 2000. In 2002, a pre-alpha version of the Tor project was introduced to the public, allowing users to anonymize their connectivity data for the Internet. The Tor project is suitable for secure browsing but also for IRC, email, and messaging services. The software operates on the onion principle. The data traffic of the Tor client is directed to a so-called entry guard, which is the entry node. This node transmits the traffic to another Tor node, a so-called relay node, that then sends the information on to an exit node, which serves as a doorway to the regular Internet.
The advantage of this approach is that none of the nodes knows all of the information about a particular connection. For example, the entry guard knows where the request originates, but not to whom it is addressed. This information is only known by the exit node, which in turn does not know where the request originates (see Figure 1). The so-called mixed cascade changes its route every 10 minutes so that the packets run continuously via new nodes. It is not known beforehand which nodes these will be; therefore it becomes extremely difficult to attack and reveal the connection.
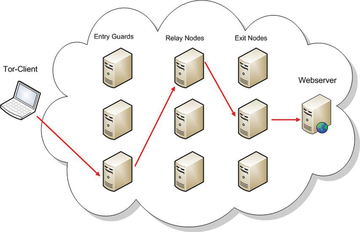 Figure 1: None of the three relay nodes of the onion routing system has complete information about a connection.
Figure 1: None of the three relay nodes of the onion routing system has complete information about a connection.
Tor, however, encrypts data only during traversal of its relay nodes. If you use the unencrypted HTTP protocol, then the information transmitted outside of the Tor network will remain visible. This means that an attacker could capture passwords that might be transmitted.
The Tor Browser
The bundle from the preconfigured Tor client and the modified Firefox browser is available in various languages [1]. After downloading the version suitable to your architecture, you can unpack the archive with
tar -xvf tor-browser-linuxVersion.tar.xz
in the terminal. Then, move the newly created tor-browser_de directory into a folder such as /opt and switch to tor-browser_en-US/Browser .
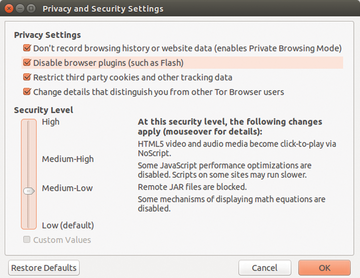
Enter ./start-tor-browser to begin setting up the software. Using its graphical user interface, the tool will first ask how you would like to make contact with the Tor network. A user with direct connection to the Internet would probably select a direct connection and click on the connect button. After accessing the network, the modified browser based on Firefox version 31.6.0 ESR will start. In the upper portion of the screen, you will find menu options for the browser security levels with a slider to set your preferences (Figure 2).
Setting the levels is important because completely blocking all of the web techniques currently in use means that much of the content available over the Internet, especially multimedia content, does not display correctly. Therefore, you should avoid pushing the slider to the maximum level of protection if you are a frequent visitor of sites with lots of optical gimmicks or multimedia content. Additionally, you will find some settings for privacy above the slider. These are already activated in order to prevent spying by tracking services.
Modification
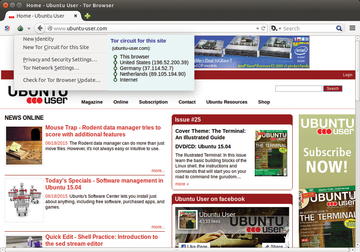
The onion symbol sits on the upper left in the browser next to the address bar. To the left of this symbol is the NoScript icon. As soon as you call up a web page and click on the small triangle next to the Tor icon, you will be able to see which route your data packets take. The route is shown next to the configuration menu and is displayed in the form of IP addresses for the Tor nodes used to transmit data as well as the location of the servers. You will also see that Tor chooses a new route every time another page is called (Figure 3).
Clicking on the icon for the NoScript add-on to the left of the Tor onion, and selecting the Options entry in the menu, opens a rather voluminous dialog containing the tools settings. The developers of the Tor bundle put a lot of careful preparation into NoScript so that the settings are not too restrictive for most websites. However, if a frequently called website doesn't appear correctly because of a lack of rights, then you should enter the URL for the affected site in the options menu under positive list . The add-on for the site will then allow scripts to execute (Figure 4).
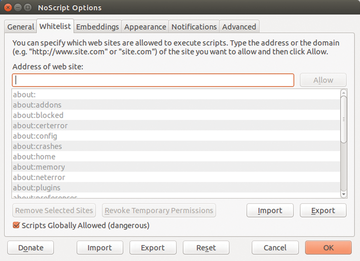 Figure 4: The NoScript add-on makes it possible to deal with the scripts embedded in the websites in a finely grained way.
Figure 4: The NoScript add-on makes it possible to deal with the scripts embedded in the websites in a finely grained way.
You can prevent Microsoft Silverlight, Adobe Flash, Java, and other programs from loading with embedded objects . Remember that overly restrictive settings will cause websites to run incorrectly. Therefore, the browser comes with this filter deactivated. The settings under extended make it possible to fine-tune the behavior of the add-ons. For this, the tool makes a distinction between trustworthy and non-trustworthy sites and defines its own rules by setting or removing checkmarks for the corresponding options.
Additionally, the HTTPS group lets you force or prevent encrypted connections for addresses that you can choose as you wish. But, because the developers of the Tor Bundle have already integrated the Firefox HTTPS Everywhere add-on, the browser already requests the encrypted version of all sites called.
The developers have even modified the customary the configuration dialog for Firefox. As a result, the basic configuration of the browser does not create a browsing history and it does not save passwords. You will find a data transmission function introduced and implemented in more recent versions of the Tor browser in the extension | data transmission tab. However, this is turned off. With this setting, the software does not send status reports to the Tor project. The preset update function in Firefox was modified so that only the search for updates in the extensions | update tab is activated. The updates themselves are not automatically installed.
Advertising and Tracking
Commercial websites can be so cluttered with banners and animated content that the user loses sight of the actual content. Many sites also load so-called web pixels that often, unbeknownst to the user, track user surfing behavior to many other sites.
Firefox offers two effective tools – in the form of the Adblock Plus and Ghostery add-ons – for dealing with these pests [2]. However, the Tor project has not yet integrated them into the bundle. It is a good idea to install these manually. You will find that the browser speeds up because unnecessary DNS queries disappear. It is also smart to add the filter subscription Social Media for Adblock Plus to prevent tracking by social media services like Facebook and Twitter.
Conclusion
The Tor browser bundle makes it possible to significantly increase the level of your privacy on the Internet. The developers have preconfigured the relevant settings very well so you won't need to worry much about manual configuration. In my test, the browser exhibited performance similar to that of the standard Firefox version. The only flaw in the bundle is the lack of the Adblock Plus and Ghostery add-ons, but you can easily fix that with manual installation that requires just a few mouse clicks.
Infos
- Downloading the Tor browser: https://www.torproject.org/download/download-easy.html.en
- Firefox Add-ons: https://addons.mozilla.org
- Adding a subscription: https://adblockplus.org/en/features