Safety First
Those wanting to surf the Internet incognito need a lot of expertise and time to secure their system. Tails saves you much of this work and lets you be online securely and anonymously.

Heider Almeida, 123RF
Those wanting to surf the Internet incognito need a lot of expertise and time to secure their system. Tails saves you much of this work and lets you be online securely and anonymously.
Securing their Internet access proves to be an insurmountable obstacle for many users. In fact, you need to put in a considerable amount of effort to make online services of various kinds immune to eavesdroppers and data leeches. However, Tails [1] is a live distribution that saves you the time-consuming process of hardening your system. Tails is also ideally suited for on the go; it doesn't affect the host being used and therefore doesn't leave any traces behind on local mass storage.
You will find the current version of Tails (1.5) as a 960MB ISO image together with a signature file on the distribution's project page [2]. However, you don't need the signature to use Tails; you can determine from the checksums whether the integrity of the ISO image has been affected [3]. The image is suitable for both 32- and 64-bit computers. After downloading Tails, either burn the image to a DVD or create a bootable USB flash drive. Alternatively, you can use an SD memory card as a medium for the Debian derivative. The developers of Tails provide a detailed manual for generating the starting medium [4].
Tails is strikingly different from the start. After the login screen appears with the question More Options? , you can answer by clicking Yes and then Forward . The distribution then offers you an option window. Here you can both create an authentication for the administrator and also modify the visual appearance of the desktop – even in such a way that makes it look like a Windows 8 user interface from a distance. Additionally, you can define a modified MAC address in this window so that the computer doesn't stand out to administrators either in passing or on the network. Once you have chosen the desired settings, you can get to the desktop by clicking the Log in button (Figure 1).
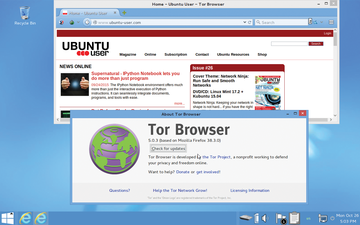 Figure 1: In stealth mode, Tails mimics the appearance of a Windows 8 desktop. The system's MAC address can also be altered on the login screen.
Figure 1: In stealth mode, Tails mimics the appearance of a Windows 8 desktop. The system's MAC address can also be altered on the login screen.
If you start it without the Windows stealth mode, the operating system will welcome you with a no-frills Gnome interface (Figure 2). Only the icons for the Tor Browser and KeePassX – a graphical application for password management – in the upper panel bar really catch the eye. A look at the submenus shows that Tails both allows anonymous Internet access and is a full-fledged Linux desktop: The applications include both LibreOffice and Gimp. Tails also provides standard programs like Audacity, Totem, and Brasero in the multimedia section. Even the desktop publishing program Scribus is available for use. Tails also includes lesser-known programs such as BookletImposer, the collaborative editor Gobby, and the audio editor Traverso.
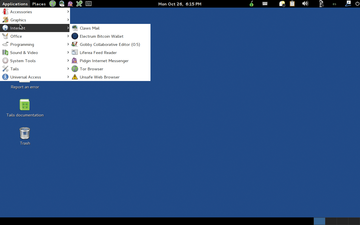 Figure 2: Tails uses a straightforward Gnome desktop by default but also has a range of privacy tools.
Figure 2: Tails uses a straightforward Gnome desktop by default but also has a range of privacy tools.
The Debian derivative also looks good under the hood: Tails provides, for example, driver modules for commonly problematic hardware components such as WiFi cards. It therefore automatically establishes a wireless connection on many devices without the need for an intricate manual installation of proprietary firmware. Although Tails is primarily intended for anonymous Internet access and secure live operation on different computers, it can still be adapted in many ways. To do this, access Tails Installer in the Applications | System Tools menu. Here, you can update a running system, and the update routine also takes into account the individually installed software (Figure 3).
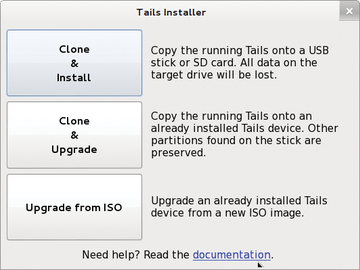 Figure 3: Tails' installation routine allows the system to be installed and updated in live operation.
Figure 3: Tails' installation routine allows the system to be installed and updated in live operation.
Tails uses the current version of Tor Browser (5.0) as the web browser [5]. It is based on Firefox 38.1.0 ESR and is hardened for using the Internet anonymously. The browser automatically establishes a connection to the Tor network when accessed and then manages all data packages using the connection. If there is a SOCKS proxy, you will find an onion icon at the top right of the Gnome desktop in the system tray. Tor Browser also uses a number of add-ons: As well as the ad blocker Adblock Plus, you will also find HTTPS Everywhere for establishing encrypted connection, and the NoScript tool for safeguarding.
If Tor Browser makes it impossible to open a website because of its restrictive settings, another browser is available. This is again Firefox 38.1.0 ESR which, in this case, establishes direct access to the Internet and allows cookies. You can find this option in the Applications | Internet option with the Insecure Internet Browser entry. This version doesn't natively use any add-ons; however, the browser is configured to secure privacy so it doesn't keep browser history.
Tails uses Pidgin with off-the-record messaging (OTR) for chatting [6]. This protocol is based on all chat protocols like Jabber, ICQ, or AIM and is considered very secure. Various chat clients also support OTR innately or through optional modules.
The email client Claws automatically uses SSL communication, meaning that your emails are transmitted securely. Furthermore, Tails allows you to encrypt emails and data via OpenPGP. Using the OpenPGP applets integrated in the system tray, it is possible, for example, to cryptographically handle texts that you want to send via email later.
To do this, open the editor Gedit from the OpenPGP applet context menu via the Open Text Editor option and write the text. Then, copy the text to the clipboard using Ctrl+C and select – again from the applet menu – Sign/Encrypt Clipboard with Public Key . Then, look for the desired key from the list in the dialog that opens and confirm the security prompt by clicking OK . You can transfer the now encrypted text using Ctrl+V from the clipboard to the email client or to the web mailer's editor section.
But Tails doesn't only take of your security when surfing the Internet. One problem that hardly attracts any attention is metadata embedded in files. Nearly all modern file formats save a variety of additional data that can provide a lot of information. For images, this includes things like the time and date they were taken, the type of camera, and the settings such as aperture, focal length, and exposure time. The location information is also included in the metadata if the camera has a GPS module – not uncommon for shots taken with smartphones (Figure 4).
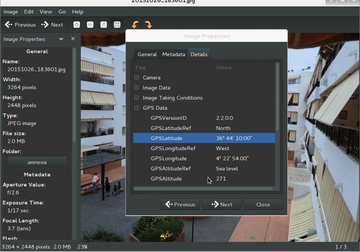 Figure 4: Many files contain invisible metadata with additional information. The location of where the image was taken can be seen from this shot taken using a smartphone.
Figure 4: Many files contain invisible metadata with additional information. The location of where the image was taken can be seen from this shot taken using a smartphone.
You can remove such metadata from a variety of file formats using the Metadata Anonymisation Toolkit (MAT [7]) without the actual file content being changed or lost. MAT doesn't even change watermarks or content steganographically embedded in files. You can find the application in the Applications | System Tools menu.
To use Tails as conveniently as possible on different machines, it is a good idea to set up a separate, persistent storage area on the USB flash drive with the operating system. This partition encrypts Tails so that the data can only be read after corresponding authentication. To create the persistent storage area, select the Configure persistent volume entry in the Applications | System Tools menu. This opens a wizard which helps you to set up the encrypted area (Figure 5).
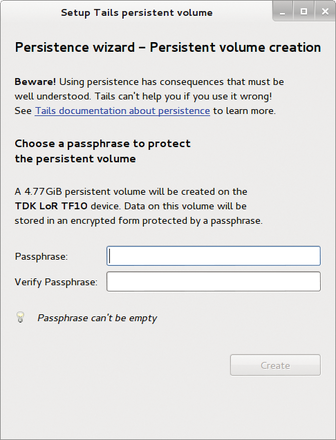 Figure 5: A wizard helps you to create a persistent memory on the memory stick. This memory is then maintained when Tails' live Linux system is restarted.
Figure 5: A wizard helps you to create a persistent memory on the memory stick. This memory is then maintained when Tails' live Linux system is restarted.
The routine automatically detects the bootable memory stick from which Tails was started – even when multiple USB devices are connected to the computer. It also expects a password to be defined for the persistent storage area being set up. Then determine which data Tails should store in the persistent area. The program provides an extensive selection list for this in which you determine the files to be stored permanently by clicking the corresponding options. The application creates the storage area once you click the Save button at the bottom right of the window. (See the "Backing Up Data" box for more.)
Backing Up Data
Note that you can only back up data on external data carriers from the current standard system, not on the internal hard drive or the host's SSD because Tails doesn't automatically integrate them into the system. If you do need to access them, define a root password in the advanced options when starting Tails. This way, you can integrate the partitions on the internal mass storage in the live system after starting Tails.
Note that this wizard only works if you have created the target medium using the Tails installer. If you Tails from a USB flash drive that you installed using a different tool, the wizard quits the service because of incompatibilities with the filesystems. In this case, you would have to clone the current operating system onto another USB flash drive using the Tails installer (Figure 6).
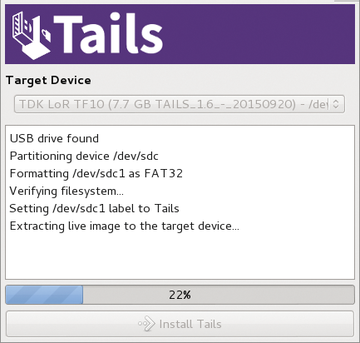 Figure 6: A prerequisite for creating a persistent drive is that you need to have created the USB stick with the Tails system using the Tails installer.
Figure 6: A prerequisite for creating a persistent drive is that you need to have created the USB stick with the Tails system using the Tails installer.
When next started, Tails also provides the option on the login screen to integrate the persistent drive so that you can access the encrypted storage area later. To do this, you need to enter the previously assigned password. The non-volatile memory is then available under the name Persistent in the file manager. If you want to delete the persistent storage area again later, call up the Delete persistent volume item under Applications | System Tools .
Like a standard Debian for package management, Tails provides the apt-get command-line command and the graphical package management tool Synaptic. You therefore have all the programs and packages from the Debian package sources at your disposal. However, because Tails is designed as a live-only system and manually installing additional software brings security risks, it requires quite a bit of overhead to permanently integrate additional programs in the operating system. Requirements for permanently installing new software include a persistent drive and an active root account, which you can set up in the advanced options in the login window when booting the system.
The APT Packages and APT Lists options must be set in the persistent storage area's configuration in the setup dialog under Configure persistent volume . If the requirements are met, open the /live/persistence/TailsData_unlocked/live-additional-software.conf file in a root terminal and enter each package to be permanently installed in a new line. After saving the file, start Synaptic, authenticate it using the root account and install the predetermined programs.
Tails doesn't do things by halves for secure and privacy-protective surfing. The distribution is also suitable for people who often use other peoples' computers and don't want to leave any traces. The Debian derivative covers many uses and has a sensible configuration, meaning that all common online services can be used immediately without your having to go through the hassle of manually customizing everything.
Tails also provides some tools for safeguarding locally stored data. Tails should therefore be the first choice for security-conscious users who don't want to harden all the applications themselves.
Infos