Finding dynamic IP addresses
Almost every network has a DHCP (dynamic host control protocol) server that dynamically assigns unique IP addresses, most of which have a limited period of validity. The server also communicates information to clients about suitable gateways and to the DNS server for name resolution. It can be difficult to keep track of the IP addresses that a DHCP server assigns on the network, but tools like Arp, Fping, and Nmap help maintain an accurate overview.
It is important to the flawless operation of the system that the defined IP block reserved for the service allow a sufficient number of addresses to be continuously assigned to all of the devices. It is especially important to have an appropriately sized IP block when setting up a public WiFi network, because an inadequate IP block can quickly lead to bottlenecks in network access and ultimately to user dissatisfaction.
When public access is essential to a setting such as a cafÈ or a co-working space, it is important to know how much adaptation is necessary and when circumstances demand it. At the same time, it is a good idea to make sure that all computers in the network have suitable settings rather than static IP addresses that can obstruct concurrent clients.
Performing an analysis of addresses that have been assigned lets the network administrator get an overview of which devices are on the network and who is regularly logging in. Sometimes this kind of analysis even reveals devices not previously detected. The primary purpose of a static analysis is to determine whether the IP address pool is sufficient. It is not necessarily meant as a means for monitoring users.
What a DHCP Server Does
The DHCP server administers a pool of IP addresses from which it draws a single address for assignment when a request comes in from a computer attached to the local network. The manages the address inventory and recognizes by reference to the MAC address which device uses which IP address. As a rule, the server assigns this data on a temporary basis. As a result, an assignment, referred to as a "lease," is in its essence a type of contract for use. Once the client no longer needs a particular address, the assignment, or lease, expires, and the address reverts to the pool to wait for re-assignment (i.e., lease renewal).
The length of time for which a lease is valid is called "lease time," which is specified when you configure the DHCP server. A typical lease time would be between 30 minutes and six hours long. The actual period of time is often determined according to the frequency of user fluctuation. A good rule of thumb is that lease times become shorter when fluctuation is greater.
A DHCP client announces its presence in the network by broadcasting to a corresponding server. The server then answers the request, and if possible, the server also offers an IP address to the client. If the client accepts the address offer, the server then assigns the confirmed IP address to the client and records the assignment [1].
Every DHCP server uses its own formatting for the file, which contains the inventory of distributed IP addresses. The integrated server for Debian from the Internet Systems Consortium (ISC) [2] creates a dhcpd.leases file under /var/lib/dhcp/ . Dnsmasq [3] on the other hand uses a /tmp/dhcp.leases file (Listing 1). One entry in the file indicates the point in time at which the lease expires, in terms of the number of seconds that have elapsed since 1.1.1970. This same entry also contains the MAC address for the client, the distributed IP address, the host name, and the client ID that has been broadcast. The ID is customarily derived from the MAC address of the network interface [4]. Hence, the commonly observed similarity between the two.
Listing 1
dhcp.leases
# cat /tmp/dhcp.leases 1456254174 a8:7b:39:95:4a:5f 192.168.22.129 Nokia-N900 01:a8:7b:39:95:4a:5f 1456251956 00:13:e8:d2:60:bf 192.168.22.213 tuba * 1456254015 00:25:90:09:9c:98 192.168.15.129 trumpet * 1456253248 00:25:90:09:a1:9f 192.168.15.130 horn 01:00:25:90:09:a1:9f
For its part, the client stores the information on the lease it has been granted and the network configuration. The ISC DHCP client places the information in the dhclient.leases file which is located under /var/lib/dhcp/ (Listing 2). Among other data, this file contains the assigned IP addresses (fixed-address ), the subnet masks (option subnet-mask ), the IP address for the router (option routers ), the lease time for the IP address (option dhcp-lease-time , which in this example is 60 minutes), the DNS server (option domain-name-servers ), the NTP server (option ntp-servers ), and the times for the expiration (expire ) and the renewal (rebind ) of the lease for the IP address. This last value determines when the client requests an extension from the server on the lease for its IP address.
Listing 2
/var/lib/dhcp/
lease {
interface "eth0";
fixed-address 192.168.55.183;
filename "/ltsp/i386/nbi.img";
option subnet-mask 255.255.255.0;
option routers 192.168.55.1;
option dhcp-lease-time 3600;
option dhcp-message-type 5;
option domain-name-servers 192.168.55.1,192.168.55.6;
option dhcp-server-identifier 192.168.55.6;
option ntp-servers 192.168.55.3;
option broadcast-address 192.168.55.255;
option host-name "efho-mobil";
option netbios-name-servers 192.168.55.4;
option domain-name "network.local network.org";
renew 2 2016/03/22 10:29:23;
rebind 2 2016/03/22 10:56:54;
expire 2 2016/03/22 11:04:24;
}
Finding the IP Addresses
The grep command-line utility helps in the hunt for IP addresses that are assigned on a network set up with an ISC DHCP server. By using the following call,
$ egrep "lease|hostname|hardware|\}" /var/lib/dhcpd/dhcpd.leases
you can determine which IP addresses are currently assigned. The output includes information, if known, about the lease, the hostnames, and the MAC address for the interface.
The network traffic provides additional clues for finding IP addresses. A computer observes data packages arriving via its interface in the same way a conveyor belt works for customers eating in a Japanese sushi restaurant. Specifically, the computer wakes up and reacts when a package is addressed to its interface directly. Almost as a side note, the computer also receives information on network occurrences, including such things as requests for address resolution sent out via the address resolution protocol (ARP) [5].
The /proc filesystem [6] for the Linux kernel provides a table containing this information. The data in the table originates in the so-called ARP cache, which the root user can read with the arp -a command (Listing 3). The output contains the IP address, the type of hardware, flags, the MAC address for the interface belonging to the IP address, and the interface from which the Linux kernel obtained the data (Listing 4).
Listing 3
Using the arp Command
# arp -a ? (192.168.55.22) at 52:54:00:8a:43:5f [ether] on eth0 lists.network.org (192.168.55.6) at 00:16:3e:18:29:b3 [ether] on eth0 ? (192.168.55.97) at bc:05:43:48:9b:81 [ether] on eth0 orange.network.local (192.168.55.1) at 52:54:00:b3:8d:be [ether] on eth0
Listing 4
ARP Cache Raw Content
$ cat /proc/net/arp IP address HW type Flags HW address Mask Device 192.168.55.22 0x1 0x2 52:54:00:8a:43:5f * eth0 192.168.55.6 0x1 0x2 00:16:3e:18:29:b3 * eth0 192.168.55.97 0x1 0x2 bc:05:43:48:9b:81 * eth0 192.168.55.1 0x1 0x2 52:54:00:b3:8d:be * eth0
The ip command-line utility has established itself as another worthwhile tool for monitoring the network. The tool is a somewhat more flexible successor to the twin utilities ifconfig and iwconfig found in the iproute2 [7] collection. The ip command displays all of the neighbors in the network via the neighbor show option. The basis for this function is the ARP cache (Listing 5).
Listing 5
ARP Cache
# ip neighbor show fe80::1:1 dev eth0 lladdr 52:54:00:b3:8d:be router STALE 192.168.55.22 dev eth0 lladdr 52:54:00:8a:43:5f STALE 192.168.55.6 dev eth0 lladdr 00:16:3e:18:29:b3 STALE 192.168.55.97 dev eth0 lladdr bc:05:43:48:9b:81 STALE 192.168.55.1 dev eth0 lladdr 52:54:00:b3:8d:be STALE
Ping and Fping
The Ping utility is also frequently used to track down computers situated on the network. However, this utility only works when the network permits transport of ICMP packets. The same restriction applies to the other tools presented here because they are based on the same protocol.
Listing 6 shows a Bash one-liner that searches for assigned IP addresses in the range between 192.168.55.11 and 192.168.55.22. The command delivers a small list of responses from the queried hosts as its output.
Listing 6
Pinging Several IPs
$ for i in $(seq 11 22); do ping -c 1 "192.168.55.$i" | grep "bytes from"; done 64 bytes from 192.168.55.11: icmp_seq=1 ttl=64 time=0.623 ms 64 bytes from 192.168.55.14: icmp_seq=1 ttl=64 time=3.64 ms 64 bytes from 192.168.55.16: icmp_seq=1 ttl=64 time=7.11 ms 64 bytes from 192.168.55.22: icmp_seq=1 ttl=64 time=0.839 ms
Those wanting to get by typing fewer entries can turn to Fping for IPv4 and Fping6 for IPv6 [8]. Listing 7 shows a call similar to Listing 6. The parameters -a and -q help restrict output to live IP addresses. The -g option generates a target list from the supplied starting and ending IP addresses. Alternatively it accepts a netmask.
Listing 7
Fping
$ fping -aqg 192.168.55.11 192.168.55.22 192.168.55.11 192.168.55.14 192.168.55.16 192.168.55.22
The Versatile Nmap Scanner
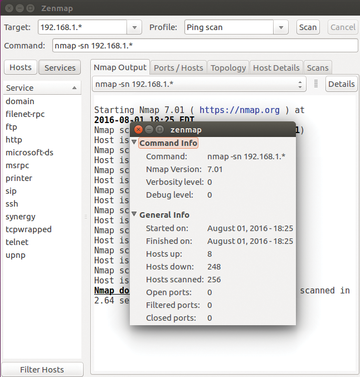
If the output from Ping and Fping is not sufficient, it is time to take a look at Nmap [9] and its graphical front end, Zenmap. Specifying the -sP conditions and the network help to fish out the IP addresses for all accessible hosts (Listing 8). If it can, Nmap also delivers the names of the hosts (Figure 1).
Listing 8
Nmap
$ nmap -sP 192.168.69.* Starting Nmap 6.47 ( http://nmap.org ) at 2016-04-25 09:54 CET Nmap scan report for 192.168.69.1 Host is up (0.00098s latency). [...] Nmap scan report for fritz.box (192.168.69.67) Host is up (0.00052s latency). Nmap done: 256 IP addresses (5 hosts up) scanned in 2.32 seconds
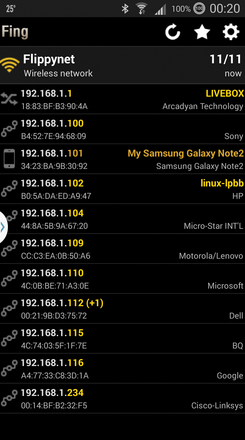 Figure 1: The graphical front end Zenmap creates a summary of the scan results from Nmap and offers additional information about each host.
Figure 1: The graphical front end Zenmap creates a summary of the scan results from Nmap and offers additional information about each host.
Finding a DHCP Server
The call dhclient -v made as root is usually a reliable way to find DHCP servers that have gone missing. A simpler method would be to use dhcping [10], which is primarily used to determine whether a DHCP server is still running. You can call this program with the -v (verbose) specification (Listing 9). The DHCPStatus [11], reportdhcp [12], and dhcpd-pools [13] tools work in a similar fashion.
Listing 9
dhcping
# dhcping -v Got answer from: 192.168.55.6 received from 192.168.55.6, expected from 0.0.0.0 no answer
Inventory of Leases
Most of the tools referenced here can be used without root rights. The Perl script dhcp-lease-list works differently. It can only be started by the system administrator. This tool has been a part of the ISC DHCP server since version 4.3.1. It uses the file for the assigned leases [14] as parameters and interprets the leases (Listing 10). The output lets you view the MAC addresses, the IP address assignments, the hostnames, the valid time of the lease, and, if available, the name of the manufacturer of the network chip.
Listing 10
dhcp-lease-list
# dhcp-lease-list --lease /var/lib/dhcp/dhcpd.leases [...] MAC IP hostname valid until manufacturer =============================================================================== [...] 00:1e:67:39:cd:fa 192.168.251.249 DALCOServer 2016-02-23 16:52:33 -NA- 00:1e:67:49:72:fe 192.168.251.6 -NA- 2016-02-23 16:52:55 -NA- 00:1e:67:4f:df:2c 192.168.251.93 DALCOServer 2016-02-23 16:52:38 -NA- [...]
Mobile
Smartphone users can turn to a commercial tool known by the name of either Look@Lan or Fing [15] for help. This tool comes as a DEB package for Android and Debian and combines Ping and Nmap. The software has versions for the command-line and a graphical interface (Figure 2).
Conclusion
As long as everything runs smoothly on a DHCP network, you do not need to waste time looking at address assignments for hosts. However, if the system experiences problems, you will find that the collection of tools presented here offers reliable help for analyzing the entire LAN infrastructure.
Acknowledgments
The author thanks Axel Beckert, Sebastian Andres, Wolfram Eifler, Dirk Deimeke, and Werner Heuser for the encouragement and helpful criticism they provided during the preparation of this article.
Infos
- DHCP: https://en.wikipedia.org/wiki/Dynamic_Host_Configuration_Protocol
- ISC DHCP server (DEB): https://packages.debian.org/jessie/isc-dhcp-server
- Dnsmasq: http://thekelleys.org.uk/dnsmasq/doc.html
- Format of lease files: http://lists.thekelleys.org.uk/pipermail/dnsmasq-discuss/2006q2/000734.html
- ARP: https://en.wikipedia.org/wiki/Address_Resolution_Protocol
- procfs: https://www.kernel.org/doc/Documentation/filesystems/proc.txt
- IP neighbor: http://linux-ip.net/html/tools-ip-neighbor.html
- Fping: http://fping.org
- Nmap: http://nmap.org
- dhcping (DEB): https://packages.debian.org/jessie/dhcping
- DHCPStatus: http://dhcpstatus.sourceforge.net
- reportdhcp: http://www.omar.org/opensource/reportdhcp/
- dhcpd-pools: http://dhcpd-pools.sourceforge.net
- An overview of DHCP leases: http://www.tcpipguide.com/free/t_DHCPLeaseLifeCycleOverviewAllocationReallocationRe.htm
- Fing mobile: http://www.lookatlan.com